Tobias Fiebig, TU Delft, WP2
Within Safe-DEED we are dealing with Secure Multi Party computation for distributed data market places. Within Workpackage2, we want to create business models to support companies in adopting MPC within their business. So what do threat-models have to do with that… and what are threat-models?
Threat-models 101
A threat-model is a structured analysis of how security principals—we measure them with ‘C-I-A’, confidentiality, integrity, and availability—might be tainted by an attacker. Confidentiality means that data is only read by authorized people (which is also important in the concept of privacy), integrity means that only authorized people can change data, and availability means that authorized people can always access data if they want to. When building a threat-model, usually for a specific system, we then delve into which assets are to be protected (in terms of CIA) and which threats may loom for these assets.
Why threat-models if you want business models?
The main reason why we are looking at threat models in the context of MPC and data marketplaces, is a concept called ‘value proposition.’ Remember, if you want companies to adopt a new technology, said technology has to add value for the ones investing in it. In terms of a security technology—like MPC—that value has to be an increase in ‘security.’ The problem here is that security is not easily measurable. We have to quantify it. Hence, we do look at the threat models for data market places with and without MPC, to see how the threat landscape changes by introducing MPC. That—if we find it—improvement is then the value proposition we can offer operators of data market places.
Challenges in threat-modelling for Data Marketplaces
The main issue with threat-modelling for generic data marketplaces is that traditional frameworks for threat-modelling assume a specific system to be in place, for which implementations and threats can be assessed. For data market places, especially with added MPC, we, however, have to analyze a generic system. Hence, we have to find a new framework to assess an abstract system.
Assessing abstract systems
For our framework, we decompose the abstract concept of data market places by its components, and these components to specific business functions. For each function, we can then investigate the specific IT assets that might suffer from threats. We can then establish a violation of C/I/A for each of these threats, the potential business consequences (impact), and draft a mitigation technique. To get an overview, please see the figure below:
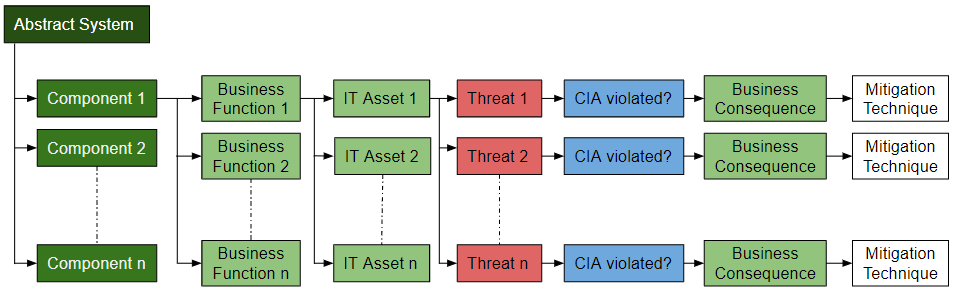
Decomposing threats to data marketplaces
Applying our approach to data marketplaces, we find six different components:
- Identity management (Authentication and Authorization)
- The Broker Service (User interaction)
- The Clearing house (Transaction repository)
- Data inventory ([Meta]Data Storage)
- Data Exchange Service (Data transfer mechanism)
- Data Analysis Services (Data analysis tools)
When we now look at these components, it becomes clear that MPC can only impact points 3-6, the data inventory, data exchange service, and data analysis services. The most crucial impact is certainly in the data inventory. With the data marketplace no longer having to store the data itself (as it is held by the participants), the threat of losing data—for whatever reasons—is transferred from the data marketplace to those providing the data. In turn, those providing the data have to no longer trust the data marketplace. Similarly, the data exchange service is influenced, as data does not have to be exchanged anymore. See the blog article from our partners from TU Graz to learn more about that. (Link: https://safe-deed.eu/methods-enabling-privacy-preserving-computations-on-customer-data/)
This all sounds very gloomy. However, there are also new threats being introduced for the data analysis services. As customers can no longer check the data, but have to trust MPC to come up with the right results, a malicious data provider may try to poison customers’ analysis pipelines. Hence, to find a clear value proposition, our technical partners will have to find reasonable methods to ensure that malicious data providers cannot poison a data analysis process. But, as they are already working on that, we are looking forward to making a MPC solid value proposition to data marketplace operators.